
How to Future-proof Your Technical Foundation
Modernize from infrastructure to platform to optimize operations and reduce burden.
Download the EbookIn today’s world, businesses are meeting face-to-face with customers less often, and it’s become crucial to carefully manage access to company resources. However, identity management is not straightforward, and many companies are struggling to better understand identity policies in a climate-driven by remote work and access needs.
This is where Identity and Access Management (IAM) comes in. Simply speaking, IAM is a framework of policies and technologies to ensure that the right users have the right access to the right resources. And it’s up to the organization and its technology partner to ensure these safeguards are optimally configured and monitored appropriately.
Why IAM is important
IAM is crucial in the modern digital world because as threats continue to evolve, no business wants to be in the headlines as the victim of the latest data breach. By implementing IAM security, companies have:
- Stronger protection than a simple username and password
- Privileges are tracked and controlled in a single window
- Accounts are denied access to information that they are not authorized to view
By combining these three, you can take the burden of security off-network access, which is more easily breached, and evaluate each access attempt individually to ensure that identity is the new security perimeter.
How IAM works
With IAM, when a user logs in, the system looks for ‘signals’ such as username, IP address, whether they are logging in from a company device, and if they are using an approved application. Based on those signals, the system determines if additional steps, such as multi-factor authentication, are required before a session is created. Finally, based on the signals, additional authentication requirements, and the permissions assigned to the user, the system will create a session that permits access to some or all company data and applications.
Many companies using Microsoft 365 (M365) or Office 365 (0365) licensing are underusing IAM features that are available with their current licensing. All tiers of M365 and O365 licensing include the basic features of Azure Active Directory which is a complete IAM solution right out of the box. Higher tiers of licensing include additional IAM features, including the ability to leverage single sign-on for third-party applications, multi-factor authentication, conditional access and sign-in risk evaluation (including the ability to leverage biometric factors for authentication), advanced identity protection, and even ‘password less’ sign-in using the Microsoft Authenticator app.
IAM components
Once an organization has licensed a comprehensive solution like Azure Active Directory, the next step is configuring the components to maximize the organization’s security strength. For the highest security, businesses should configure conditional access policies that include both user and sign-in risk evaluation. In addition, administrative accounts should have Azure AD Privileged Identity Management (PIM) configured, which is Microsoft’s privileged access management solution. More on that later in this post.
Conditional access controls
Conditional access is the mechanism that Azure Active Directory uses to decide whether a user should be allowed to log in, what additional actions should be required, and what controls should be placed on their session. The following diagram illustrates this process:
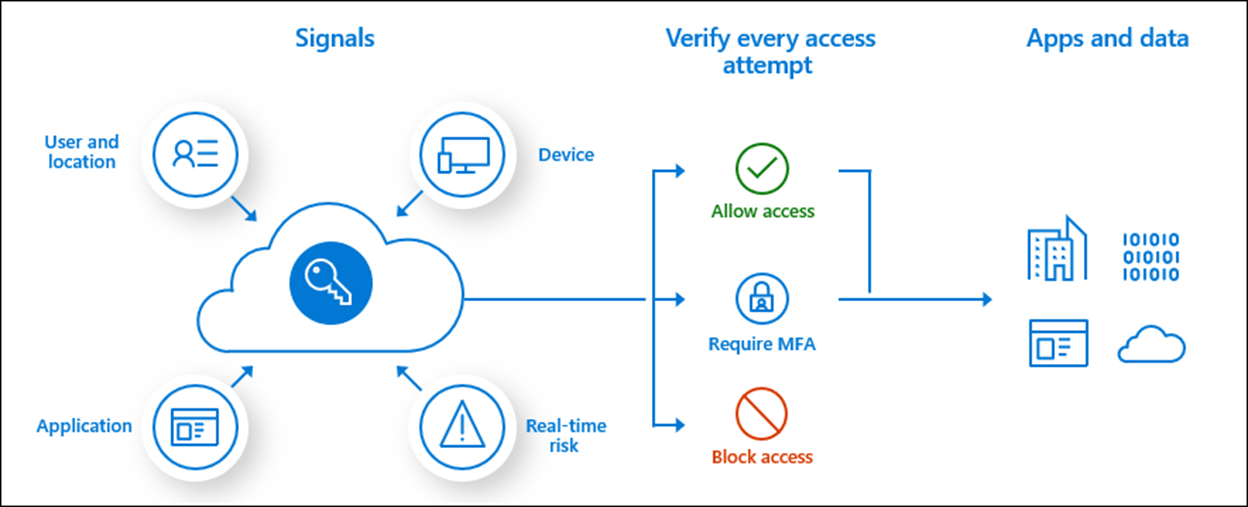
Although this diagram is simplified, conditional access allows you to require additional user and device controls when verifying each access attempt, as well as applying session controls to limit access to apps and data after access is approved.
Privileged Access Management (PIM)
Once conditional access for accounts with administrative privileges has been set, applying PIM policy is the next step. PIM follows the principles of zero standing access and least privilege, also known as just-in-time access. When a user needs to perform an administrative action, PIM can grant that user the appropriate administrative role for a set period. When configuring PIM policy, you can require steps such as approval from a manager, multi-factor authentication, and documented justification (which can contain a reference to an approved change request).
PIM provides a window for audit history and streamlining access reviews – both of which should be components of any modern security position.
Risk evaluation
IAM splits risk evaluation into two categories for use in conditional access: user risk and sign-in risk. User risk identifies leaked credentials found online for a specific account, while Azure AD Threat Intelligence indicates whether unusual activity for a given account matches previously identified attacks by Microsoft’s threat intelligence sources.
In addition to user risk, sign-in risk is calculated using the following factors:
Source IP address
- VPN, TOR, etc.
- Malware linked IP
Geographic anomalies
- Impossible or atypical travel
Application usage
- Suspicious inbox rules or forwarding
Password spray
Finally, once each type of risk is categorized as being high, medium, or low, that information is used by conditional access policies and Azure identity protection to pinpoint potentially compromised accounts.
FAQs
How can my business leverage IAM without increasing my operating expenses or technical debt?
- By using conditional access with risk evaluation, you can securely enable common actions such as self-service password reset. This reduces the calls to your helpdesk, which helps offset additional operating expenses as well as reduce the burden of support.
My business is resistant to change, how do we get started?
- IAM can be applied to individual groups within your organization, which allows you to run a pilot program and slowly roll out changes across your organization. By slowly raising your identity security position, even change-resistant organizations can reap the benefits of IAM.
Learn more about how IAM can be an integral part of your organization’s security strategy. Our expert security team is on hand to answer questions, assess security needs, and work with you to help better protect your employees, customers, and data.


